Zero Trust Network Overview 2025. This combination of authentication, policy enforcement, and. Zero trust architecture (zta) has emerged as a critical framework for securing modern enterprises.
The zero trust security model is a way to minimize both internal and external threats to company data by segmenting. Zero trust is a concept that can be paraphrased as never trust, always verify. a zero trust architecture (zta), as described by the american national institute of standards.
Zero Trust Network Overview 2025 Images References :
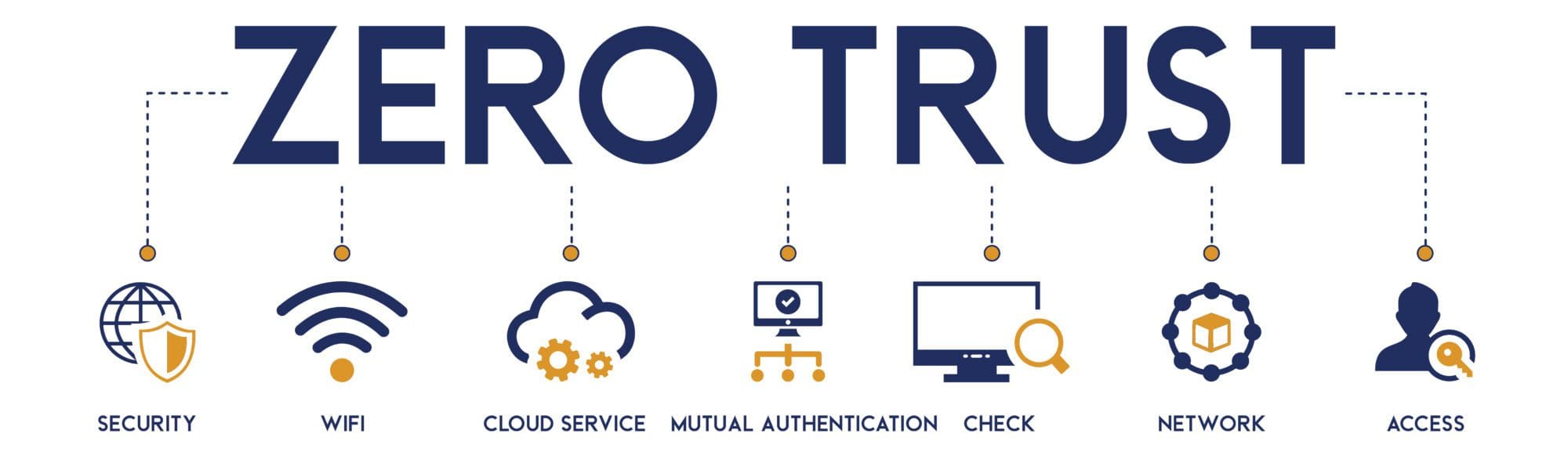 Source: www.imagequest.com
Source: www.imagequest.com
Zero Trust Security Zero Trust Network ImageQuest Blog, Experts have called for more widespread implementation of zero trust architecture frameworks.
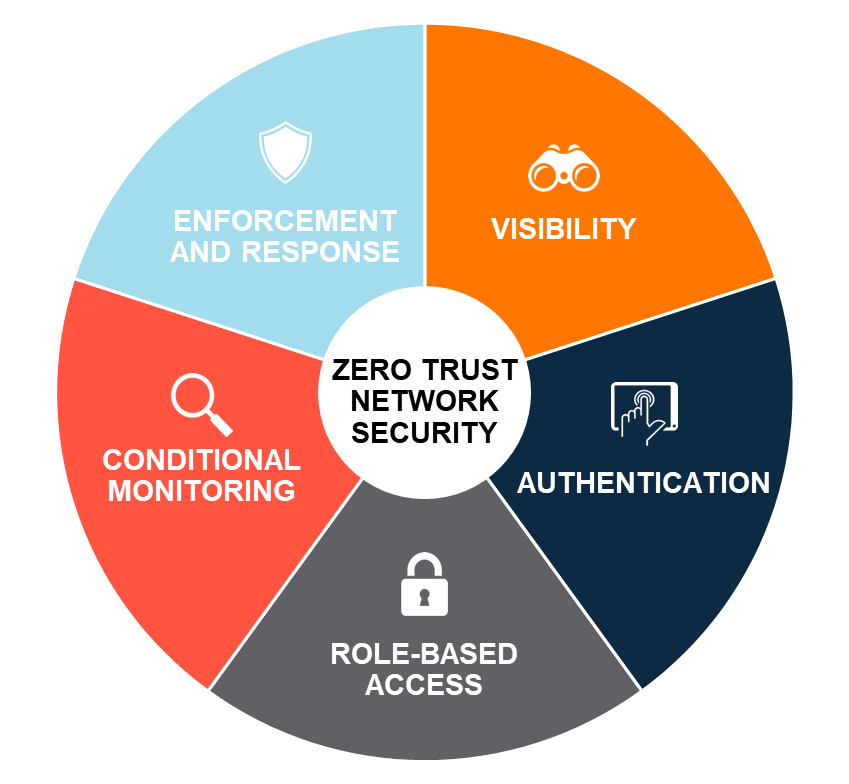 Source: blogs.arubanetworks.com
Source: blogs.arubanetworks.com
Protecting the organization with Zero Trust network security Aruba Blogs, Enter zero trust—a security framework designed to protect businesses by assuming that no entity, whether inside or outside the network, can be inherently trusted.
 Source: blog.greencloudvps.com
Source: blog.greencloudvps.com
What is Zero Trust Network Access (ZTNA)?, Zero trust architecture stops cyberattacks in four key ways (some of which we've already mentioned):
 Source: www.ssltrust.com.au
Source: www.ssltrust.com.au
Understanding Zero Trust. What is it? SSLTrust, For example, zero trust requires continuous.
 Source: www.goodaccess.com
Source: www.goodaccess.com
Zero Trust Network Access Explained, Zero trust architecture (zta) has emerged as a critical framework for securing modern enterprises.
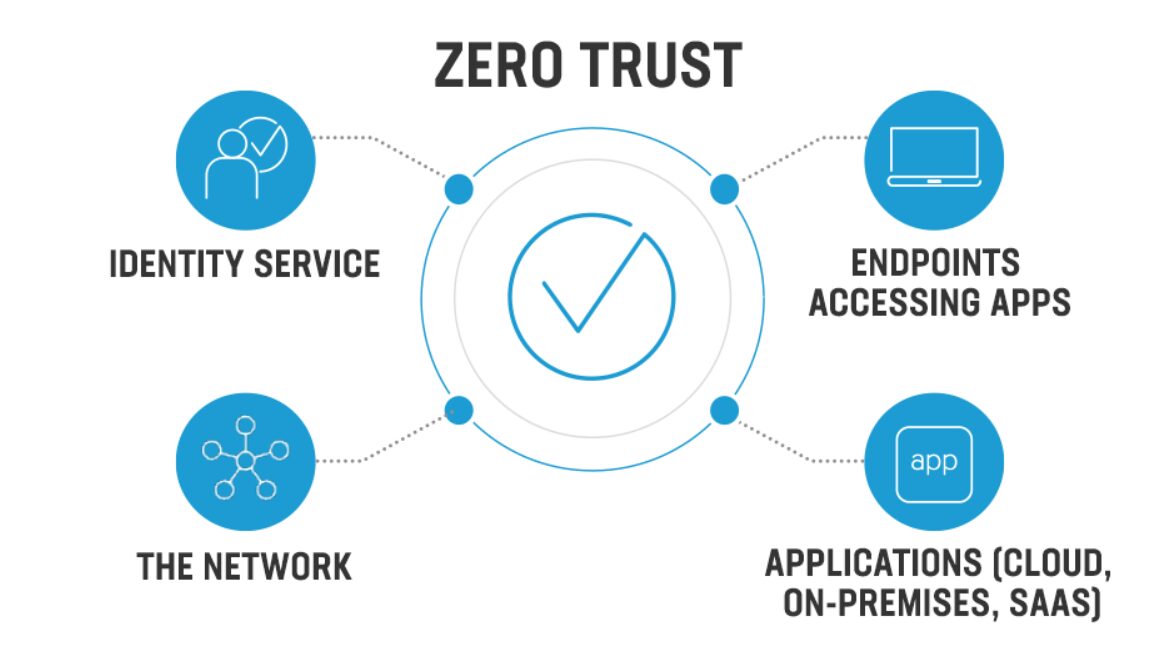 Source: selfoy.com
Source: selfoy.com
How To Implement A Zero Trust Network., By 2025, zero trust will not only be a cybersecurity framework but also a standard for modern digital ecosystems.
 Source: www.slidegeeks.com
Source: www.slidegeeks.com
Zero Trust Network Access User Flow Overview Mockup PDF, Zero trust architecture stops cyberattacks in four key ways (some of which we've already mentioned):
 Source: www.gartner.com
Source: www.gartner.com
Zero Trust in the Public Sector An Implementation Guide, Learn how zero trust is.
 Source: www.remote.it
Source: www.remote.it
Zero Trust Network Access Best Practices, As we progress through 2025, zero trust is expected to become even more integral to cybersecurity strategies.
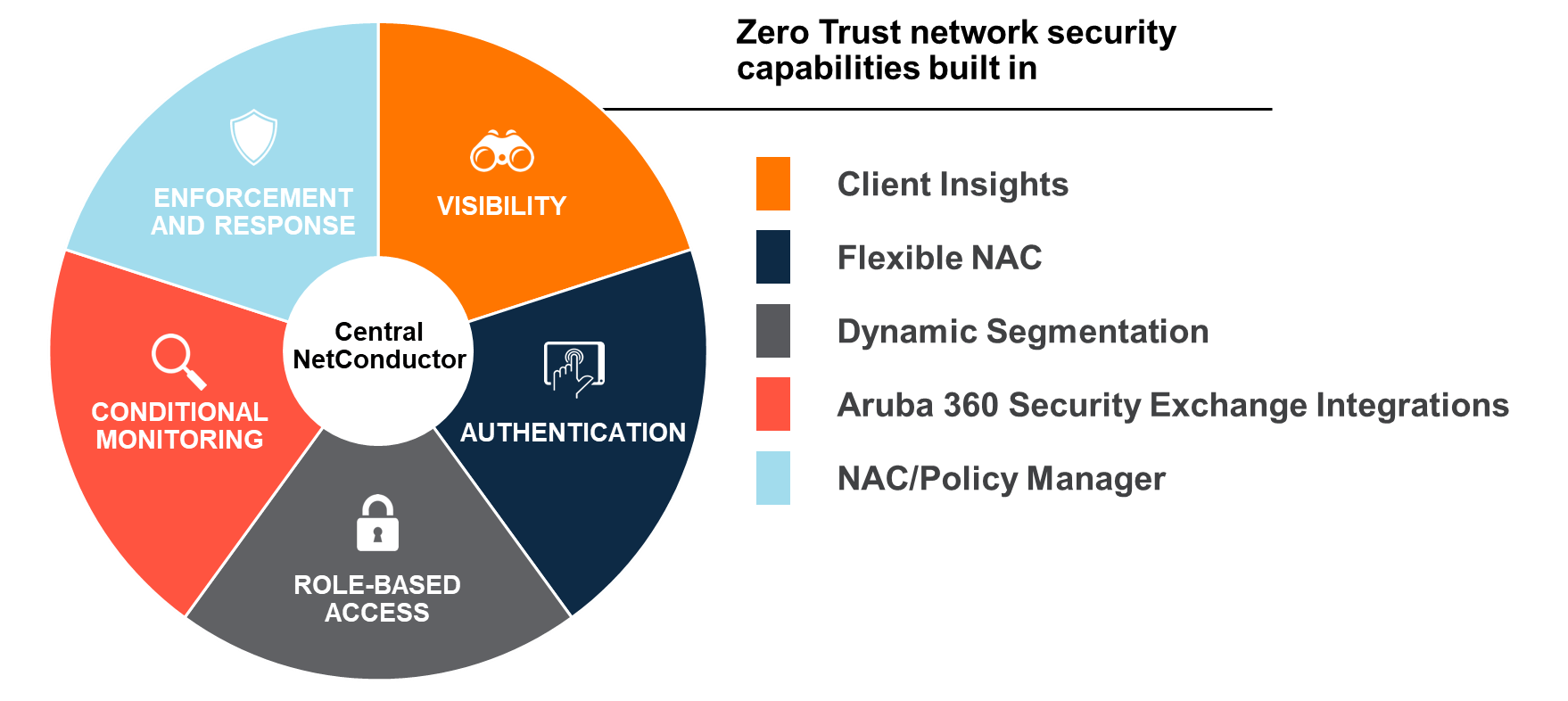 Source: blogs.arubanetworks.com
Source: blogs.arubanetworks.com
The five capabilities required for Zero Trust network security Aruba, By 2025, zero trust will not only be a cybersecurity framework but also a standard for modern digital ecosystems.